We talk about security a lot in the articles, but we talk about it even more internally as it’s vital we maintain safe and secure sites for our clients.
The threat intelligence team at WordPress security experts Wordfence have recently released their annual report on the state of WordPress’ security. As hosts of many WordPress sites we have to understand the ever changing landscape in which these sites exist so we can combat likely intrusion points..
The key take-aways from this year’s report were:
An Increase in Vulnerabilities Reported
That sounds bad – more vulnerabilities means more problems? Not quite. There has been an increase in companies who are CVE Numbering Authorities. CVE stands for “common vulnerabilities and exposures”, and is a publicly available catalogue of known security flaws. Historically many WordPress issues were not reported but because of the increase in the number and openness of these authorities, it’s made it much simpler for people to officially disclose security problems.
As WordPress, and the majority of its plugins, are built within the open source ecosystem, anyone can download the code and analyse it. The more people who are looking, the more issues the more are likely to be found. Finding and reporting such issues is increasingly becoming a full-time (paid) occupation for many developers who are then paid through the “bug bounty” programs. These ensure that the bugs don’t end up in the hands of malicious entities therefore these being responsibility reported helps everyone within the ecosystem.
Out of the vulnerabilities reported the most common issue was Cross-Site Scripting (XSS), with over 1,100 reports in 2022 alone this accounted for nearly half of all vulnerabilities disclosed. Cross-Site Scripting attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. More than a third of the XSS issues required administrative permissions on the website itself in order to be successful, so the risk was greatly reduced. This does highlight why users should only be provided with the minimum level of access they absolutely need, WordPress has a strong permissions architecture with varying roles with Contributor, Author, Editor, Shop Manager and Administrator being the most common each with different abilities.
Despite the number of reported XSS vulnerabilities there were around 3 times as many SQL injection attacks as there were XSS. A SQL injection attack is when an attacker tries to run database commands through a website which has not taken care to sanitise what people are entering into forms etc. There was also a comparable number of malicious file upload or inclusion attacks, these might be where someone gains access to the administration area and uploads a script to gain them further access rather than the intended image or text.
Re-Using Passwords
There are more and more leaked password lists available online as more data breaches occur. Credential stuffing is where hackers are utilising usernames and passwords taken from these lists to try and log in to the admin area of your site. When directories like HaveIBeenPwned (enter your email to see what leaks your info has been a part of) over 12 billion compromised sets of credentials it is no wonder that Wordfence collectively blocked over 159 billion login attempts in 2022. Surprisingly, this is actually a slight decrease on 2021.
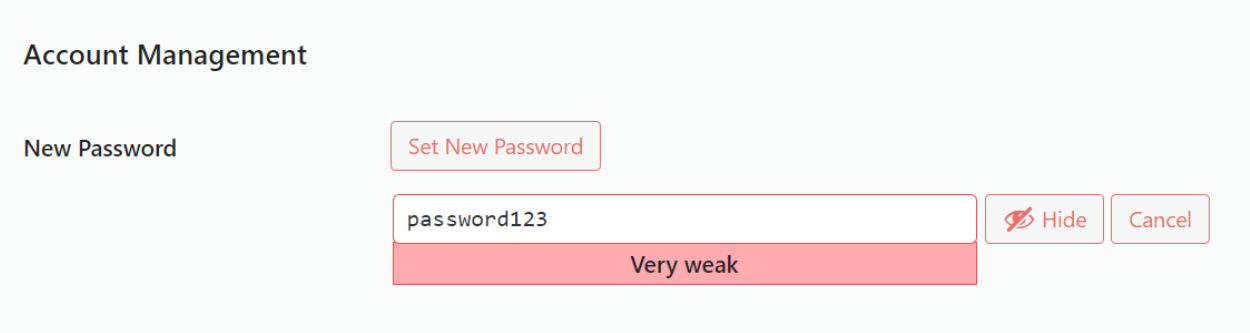
To keep your site safe please don’t use your WordPress login details on any other site, and make sure that when you create the password it is rated as Strong. These are good principals to apply to any site, and combining it with multi-factor authentication wherever it’s available will make it even more secure.
Updates & Maintenance
It has always been important to make sure that the core WordPress code, its plugins, and themes are kept up to date with the latest patches and it is no less true now. It’s obviously good practice for keeping your site secure, but also for extending its overall lifespan. Trying to upgrade very out of date plugins or WordPress code is very time consuming.
WordFence saw that most attacks targeting specific vulnerabilities were via known, and easily exploitable, flaws in this code on sites that had not received any recent updates. Infotex will take care of your site and make sure that it’s got the latest patches to keep things running smoothly. Indeed Wordfence stated “As such, the greatest threat to WordPress security in 2022 was neglect in all its forms“.
Webshells & Configurations
The second largest category of attacks was from known malicious “User Agents”. A “User Agent” is the formal term for a browser but also encompasses many other ways in which website content is processed. From Infotex’s own data around 60% of all requests are typically non-human in nature.
In addition to the more legitimate search engine robots (aka “bots”), many of these requests are from bot’s that have no purpose on a site or system other than to attack it.
A common task for these bots is looking for webshells – this is where an attacker has gained a foothold within a website and is intended to allow them to retain control and request the server to act on the attackers behalf, it’s commonplace for attackers to compete for access to webshells as nefarious access to one can cause huge problems for the site’s owner. Wordfence saw over 23 billion attacks of this type in 2022 across the 4 million+ sites they protect.
The full report is available to download via Wordfence.com



